Unit 7: Computer Engineering Technology: Networking & Programming
This unit will focus on computer networks, IP addressing, data routing protocols, services, programming languages, and concepts.
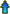 Unit 4, Act. 1: Computer Networks
Unit 4, Act. 1: Computer Networks 
Situation:
Looking at how computers work, servicing them, how they work with data internally, controlling them using programming leaves one main element which is computer networking or how computers communicate to each other locally or over the Internet.
Problem/Challenge:
Students will look at what computer networks are, network layers, IP addressing, and data routing protocols related to computer networking in general. A practical project terminating Cat 5 twisted pair cables for computer to wall jack will be done using appropriate connections, tools, and testing process.
Investigation/Ideas:
Key Terms

Here are some common jargon and terms related to networking that will help with understanding networking concepts:
- Connection is an established link through procedural protocols encapsulating the data that is transfered through a network and reconstructed at the other end
- Packet is the most basic unit (envelopes/pieces of data) that is transfered over the network that include a header of information such as source and destination, timestamps, network hops, etc with the main portion being the data itself.
- Network Interface is any software that works with your networking hardware (physical or virtual)
- LAN stands for "local area network" and refers to network or part of a network that is not publicly accessible to the general Internet, for example a home or small office
- WAN stands for a "wide area network" which means a much more extensive, larger, broader span network generally meaning the Internet as a whole and means that you would be reachable through the Internet also
- Protocol is a set of rules and standards that define a language that devices use to communicate. There are many protocols used in networking often implemented in different layers. For example some low-level protocols are TCP, UDP, IP and ICMP with some common application layer protocols built on these lower protocols such as HTTP, SSH, TLS/SSL, and FTP
- Port is an address location on a single computer that is linked to a specific software, i.e. not a physical interface or location that allows your server to communicate using more than one application
- Socket is a IP address and Port used by another computer to send data to one particular computer's specific software, see difference between a Port and a Socket and this quick guide on Ports and Sockets for more info
- Firewall is protection for your computer made up of a program using a previously implemented rules to allow or block data/traffic on specific ports
- NAT stands for "network address translation" which is a way to translate incoming requests to a routing server to the related devices/servers that know about it, usually in the physical LAN (through one IP address to the necessary back-end servers)
- VPN stands for "virtual private network" is like a private security tunnel through the Internet connecting two separate LAN computers often connecting remote systems as if they were on a local network
Computer Networks
Investigation/Ideas points:
- Point 1
- Point 2
Network Layers
Networking is often thought of as a direct horizontal connection between hosts, but how it connects is through a number of vertical layers of multiple technologies and protocols. Each layer has it's own "wrapper" around the data to help decide what to do with the data going from source to destination.
Open Systems Interconnect model (OSI)
The OSI (Open Systems Interconnnect) model shows you seven separate layers of network communication for data transfer:
- Application Layer is the one users and applications interact with the most which include protocols that focus on process to process communication across an IP network and provides a firm communication interface and end-user services such as displaying received information to the user
- Presentation Layer can be viewed as the translator for the network and is responsible for mapping resources and creating context used to translate lower level networking data into data that applications expect to see
- Session Layer is a connection handler that creates, maintains, and destroys connections between nodes
- Transport Layer is responsible for handing the layers above it and ensures that the data is delivered error-free, in sequence, and with no losses or duplications
- Network Layer is used to route data between different nodes on the network and uses addresses to be able to tell which computer to send information to
- Data Link Layer is used as a method of establishing and maintaining reliable links between different nodes or devices on a network using existing physical connections
- Physical Layer is the lowest layer of the OSI model that is responsible for handling the actual physical devices that are used to make a connection which involves the software that manages physical connections as well as the hardware itself, like thee Ethernet
(This layer can also resend information that has been dropped or corrupted and acknowledge the receipt of data to remote computers.)
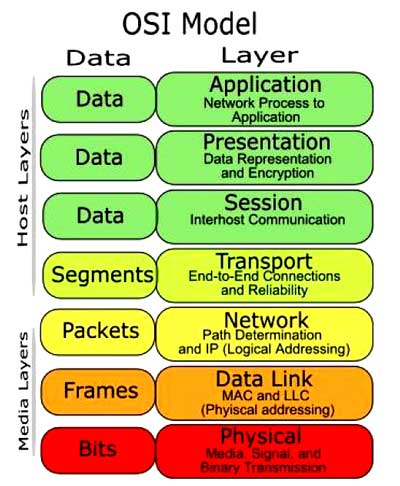
As you can see there are several different layers that can be looked at as part of the transfer of data. The TCP/IP model is a simpler model that has been widely adopted which defines only four separate layers some of which overlap with the OSI model.
- Application Layers provides applications the ability to access the services of the other layers and defines the protocols that applications use to exchange data such as Hypertext Transfer Protocol (HTTP, File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP) and Telnet with other layers to also help with use and management of the TCP/IP networks such as Domain Name System (DNS), Routing Information Protocol (RIP), and the Simple Network Management Protocol (SNMP)
- Transport Layer is responsible for providing the Application layer with session and datagram communication services using core protocols Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP)
- Internet Layer is used to package and route data between different nodes on the network and uses addresses to be able to tell which computer to send information to
- Network Interface Layer is used as a method of establishing and maintaining reliable links between different nodes or devices on a network using existing physical connections
IP Addressing

We looked at binary numbers in the last unit, so remember that IP addresses are made up of 4 segments of bits which represent the the common current IP addresses that we commonly use.
IP address, or "Internet protocol address", is a unique identifying number given to every single computer (X-box game systems, cell phones, fax machines, etc.) on the Internet This special number is used for identification, as it shows ownership, allows it to be located by other machines, and is tracked for peoples safety. To also clarify, IP address is different from a DNA (Domain Name Address) or a MAC (Media Access control) address
Right now the Internet uses mostly IP version 4 (IPv4) with its 32-bit address size. As the Internet has run out of new large blocks of IPv4 addresses, there is increasing pressure to convert to IPv6, with its 128-bit address size. It has been slow, however, and delaying of IPv4-address markets and NAT (Network Address Translation) which multiple hosts can share a single public IPv4 address, have allowed IPv4 to continue. As of April 2013, instead of 4.3 billion possible IP addresses, IPv6 will give us 34,000,000,000,000,000,000 billion possible IP addresses. Except for the change in address structure, there are relatively few differences in the routing models of IPv4 and IPv6.
IP Addresses for web servers is invisible and translated into a English domain name for ease of use. IPv4 consists of four number segments while IPv6 is made up of 8 segments. Internet authorities stock a large bundles of IP addresses for Internet service providers (ISP) which then assign to every server and Internet user that logs on. Prior to the World Wide Web becoming very popular in thee 1990's, computers were assigned static IP addresses, but with so many users, ISP's now lend the IP addressees from a block of numbers which are known as dynamic IP addressing and works better for individual users.
- Point 1
- Point 2
Routing Protocols
Investigation/Ideas points:
- Point 1
- Point 2
header
Investigation/Ideas points:
- Point 1
- Point 2
Useful Utilities
There are many useful network programs for probing and diagnosing networks and the following are some common:
pingto determine if another machine is availableipconfig(windows),ifconfig(linux and Mac), andip(newer Linux) finds your own IP addressnslookukp,digandhostare all used for DNS look-ups, each varying in convenience and optionstraceroutlists the route from you to a remote hostroute,route print(Windows),ip route show(Linux), andnetstat -r(all systems) display the host’s local IP forwarding table- Here is a cheat sheet showing some related networking information
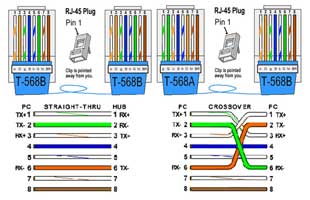
Network Cabling and End Termination
Connecting computers to the network requires a ![]() common Cat5 cable, 3.45 with RJ45 connectors. You can purchase smaller patch cables with manufactured ends or buy a roll of Cat5 cable and prepare the ends yourself. Custom cabling lengths and connections requires you manually make your own end terminations. Other situations may be that you need to replace a broken end off a long cable. In a
common Cat5 cable, 3.45 with RJ45 connectors. You can purchase smaller patch cables with manufactured ends or buy a roll of Cat5 cable and prepare the ends yourself. Custom cabling lengths and connections requires you manually make your own end terminations. Other situations may be that you need to replace a broken end off a long cable. In a ![]() switch/hub home/small office, 844, you will usually find cables will come into room, and then ends are punched into a patch panel board from the back and then use small patch cords going from this patch panel to the switch (distribution network device). This allows for quick switch upgrades.
switch/hub home/small office, 844, you will usually find cables will come into room, and then ends are punched into a patch panel board from the back and then use small patch cords going from this patch panel to the switch (distribution network device). This allows for quick switch upgrades.
Below are some related pictures showing a white box server, half size rack, punch panel, Cat6 termination, and testing. These are pictures showing my last server build and doing my own custom terminations using the unofficial Cat6 cable termination process. It is a little harder as you are using a larger gauge wire/cable to work with.
Process is pretty straight forward to ![]() terminate Cat5 cable to an RJ45 end connector, 6.33. There are three types of connections with the most common, straight cable connection, to connect the computer to a wall outlet. This Wiki How guide shows your the steps with pictures and instructions on the termination process, along with
terminate Cat5 cable to an RJ45 end connector, 6.33. There are three types of connections with the most common, straight cable connection, to connect the computer to a wall outlet. This Wiki How guide shows your the steps with pictures and instructions on the termination process, along with ![]() computer networks prezi which has a focus on network cabling with a embedded video at the end showing Cat5&6 terminations.
computer networks prezi which has a focus on network cabling with a embedded video at the end showing Cat5&6 terminations.
Resource links
Here are some resource links you can use to further review in detail related networking topics:
 History of the )nternet 48s
History of the )nternet 48s  Basic networking 117s
Basic networking 117s Networks Part 1 34s
Networks Part 1 34s Networks Part 2 20s
Networks Part 2 20s Computer Networks 31s
Computer Networks 31s- Intro to networking v1
- Intro to networking v2
- Intro to networking v3
- Intro to networking v4
 Intro to networking v5, 23p
Intro to networking v5, 23p- Computer Networking
- Beej's Network Programming
- Computer Network Basics
- Networking tutorial
- The TCP/IP guide
- Network Security
- Elements of Networking 35s
 Networking index of videos
Networking index of videos- Robert's Virtual Networking
- Networking Concepts
- Network - IPv4
- Network - IPv6
- More on IPv6
- IPv6 Tutorial
- Test your IPv6
- Online Cisco Training
 Cisco Video Training
Cisco Video Training Computer networks 14-740
Computer networks 14-740 Computer networks 5e
Computer networks 5e Computer Networking PL40
Computer Networking PL40 Data Communication PL41
Data Communication PL41 Computer Networks PL40
Computer Networks PL40- Cisco CCNA Training
 Packet Tracer 6.2
Packet Tracer 6.2- Packet Tracer download
 GNS3 for network sims.
GNS3 for network sims. CBT Nuggets
CBT Nuggets- Network Troubleshooting 57s
Create/Construct:
Create/Construct points-steps:
- Using your Raspberry Pi, find the ping from your workstation to this web site, then using the ipconfig dos windows command find out the ip address of your station and document both.
- Using tutorial guides control your Raspberry Pi GPIO outputs from either another Raspberry pi, or from your phone, or from another computer
- Create a twisted pair Cat5 patch network cable to connect from the computer to the wall jack and confirm proper operation with a test
Evaluation:
Complete your review questions, practical network exercises, and network end terminations for full marks.

| Evaluation Breakdown Component Descriptions | Marks |
|---|---|
| Always double check that you have completed all components for full marks. | Review Questions - Complete all review questions | 20 |
| Network Exercises - Ping and Ipconfig exercises | 10 |
| Raspberry Pi Networking - Demo control of output over the network | 30 |
| Cable End Terminations - Cat5 cable ends and testing | 20 |